If you’re getting calls with Caller ID tags like “fraud risk,” “spam” or “scam likely,” don’t be alarmed. This is just your carrier’s way of protecting you from robocalls.
Related:
- How to Block Spam Calls, Texts, and Emails on an iPhone
- How to Stop Robocalls on Your iPhone Right Now
- How to Block Unwanted Calls and Text Messages on Your iPhone
- iPhone Calls Going Straight to Voicemail: The Best Fixes You Can Try Today
With that being said, there are still a number of users who are confused or concerned about the new call filtering systems built into your smartphones.
To help put your mind at ease, here’s everything you should know about the systems.
Contents
Caller ID Tags and iPhones
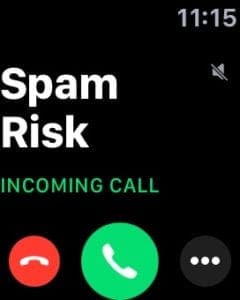
Pretty much every major carrier in the U.S. is currently in the midst of implementing anti-call spoofing measures.
These measures appear to be rolling out fairly slowly across the U.S. And despite news releases and media coverage, many carrier customers are still unaware of them.
Because of that, there does appear to be some confusion. Take this post, for example.
At least one user took the AT&T Alert: Fraud Risk tag as a legitimate call from AT&T ostensibly warning them of fraud. The user called the number back.
But you can easily avoid any mistakes with identified spam calls. If you receive any call that says “spam risk,” “fraud risk,” “possible scam” or other variations on the caller ID tag, we highly recommend letting it go to voicemail.
Legitimate callers with a valid and important reason to contact you will usually leave a voicemail. So check your voicemails to see if they did. (Some scammers will leave voicemails, but we’ll get to that in a bit.)
If the caller doesn’t leave a voicemail, then it’s probably best to leave it. The call is likely a robocall, spammer or, worse still, someone attempting to phish your information via number spoofing.
You shouldn’t call them back or answer any additional calls from the same number.
A Note on Phishing
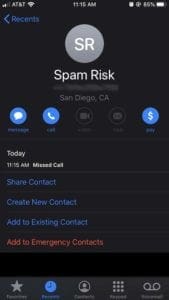
It’s worth noting that some spam or fraud calls will also leave a voicemail. Just because a voicemail is left doesn’t mean that it’s a legitimate call.
Whether or not a call is legitimate is really up to you to decide. But we highly recommend taking a few steps to avoid phishing or vishing scams.
- Never give out any sensitive or personal information to someone over the phone. That includes financial information, name, address or anything else you wouldn’t want to end up in the wrong hands.
- Don’t be fooled by scare tactics. Most phishing attempts will rely on a sense of urgency — like your account being compromised or a large payment that you “owe.”
- If all else fails, the best scenario is to ignore any voicemails from an origin you can’t verify. If the caller says they’re from Apple, the IRS or your bank, call those institutions back directly using a verified number found on their websites. Do not call just the number you received on your phone.
- If the same phone number is constantly pestering you, block them.
How Are Carriers Determining This?

Carriers are determining these spam and fraud risk calls using a network-level protection amusingly called SHAKEN/STIR.
Signature-based Handling of Asserted Information Using toKENs (SHAKEN) and Secure Telephony Identity Revisited (STIR) are interconnected protocols that authenticate whether a call is being spoofed.
The SHAKEN/STIR system doesn’t block calls — it only identifies that they are indeed originating from the number that they purport to be.
That helps mitigate the risks of number spoofing, such as calls coming from a number in your area code. It can also help cut down on numbers that are spoofed to look like they’re coming from a legitimate entity, such as Apple or another tech firm.
A Note About Accuracy
Of course, the SHAKEN/STIR method isn’t perfect. And that can result in inaccurately tagged calls on your device.
That may mean legitimate calls are flagged, but it could also mean fraudulent calls actually get through to you.
In any case, we recommend letting your carrier know about the improperly identified calls. The exact method will vary by carrier, so look up the specific directions that apply to your network.
What Other Options Are There?
The call authentication method of mitigating scam and spam calls is fine. But it’s far from the only way to deal with those annoying callers. Here are some other things you can try.
Call Blocking and Identifier Apps
Most carriers also offer actual call blocking apps, like AT&T’s Call Protect, Verizon’s Caller Name ID and T-Mobile’s built-in Scam ID and Scam Block options. There are also third-party call blocking options available, like Nomorobo or Call Control.
Another potential option you can try is TrueCaller.
Importantly, most of these options actually offer some type of call blocking measures. Anything based on the SHAKEN/STIR protocol will identify spammy calls, but won’t automatically block them.
Of course, most robust call blocking apps aren’t free. You’ll either have to pay a premium on your carrier bill or purchase an in-app subscription to access most call blocking features.
The iOS Silence Unknown Callers Feature
You can also enable a special feature that will send all unknown callers to voicemail. You can enable it by going to Settings > Phone > Silence Unknown Callers.
Wrapping Up
Having spam calls is annoying enough, so it’s natural that you may feel concerned if you see a message on your phone suggesting that a risky number is trying to ring you. Fortunately, you don’t need to tolerate these callers if you don’t want to.
While the feature on your iPhone will allow you to identify dangerous and irritating calls, you can also take the initiative. Downloading third-party apps is one way to do this, and those will help you determine who’s trying to ring you. On top of that, you can use the Silence Unknown Callers feature.
We hope that you found this information helpful. Please let us know if you have any questions or comments.

Mike is a freelance journalist from San Diego, California.
While he primarily covers Apple and consumer technology, he has past experience writing about public safety, local government, and education for a variety of publications.
He’s worn quite a few hats in the journalism field, including writer, editor, and news designer.








Write a Comment